WannaCry ransomware attack: Government ‘sure as possible’ that North Korea behind attack
UK Government Home Office Minister Ben Wallace told BBC Radio 4's Today programme that the Government believed “quite strongly” that the attack came from a foreign state and was: "as sure as possible" that North Korea was behind the attack.
His comments came as the National Audit Office released its investigation by the Comptroller and Auditor General into the WannaCry cyber attack and the NHS in England. Among the investigation’s findings are that critical alerts had been issued to patch systems to prevent WannaCry in March and April 2017, the full extent of and costs of the disruption are unknown, and all organisations infected by the ransomware shared the same vulnerability and could have taken relatively simple action to protect themselves.
WannaCry encrypts data on infected computers and demands a ransom payment to allow users access. The computer virus was released worldwide on Friday, May 12, 2017. This was the largest cyber attack to affect the National Health Service (NHS) in England and affected services in the week from May 12 – 17, although individual trusts had been attacked before May 12 – two of the trusts infected by WannaCry had been infected by previous cyber attacks.
One of England’s biggest trusts, Barts Health NHS Trust, had been infected before, and Northern Lincolnshire and Goole NHS Foundation Trust had been subject to a ransomware attack in October 2016, leading to the cancellation of 2,800 appointments.
The National Audit Office investigation focused on the ransomware attack's impact on the NHS and its patients; why some parts of the NHS were affected; and how the Department and NHS national bodies responded to the attack.
The Department of Health (the Department) and NHS England worked with NHS Digital, NHS Improvement, the National Cyber Security Centre, the National Crime Agency and others to respond to the attack.
The Department was warned about the risks of cyber attacks on the NHS a year before WannaCry and although it had work underway, it did not formally respond with a written report until July 2017, says the report. The Department and Cabinet Office wrote to trusts in 2014, saying it was essential they had "robust plans" to migrate away from old software, such as Windows XP by April 2015.
In March and April 2017, NHS Digital had issued critical alerts, warning organisations to patch their systems to prevent WannaCry. However, before May 12, 2017, the Department had no formal mechanism for assessing whether local NHS organisations had complied with this advice and guidance and whether they were prepared for a cyber attack.
The attack led to disruption in at least 34 per cent of trusts in England, according to the investigation, although the Department and NHS England: “Do not know the full extent of the disruption.”
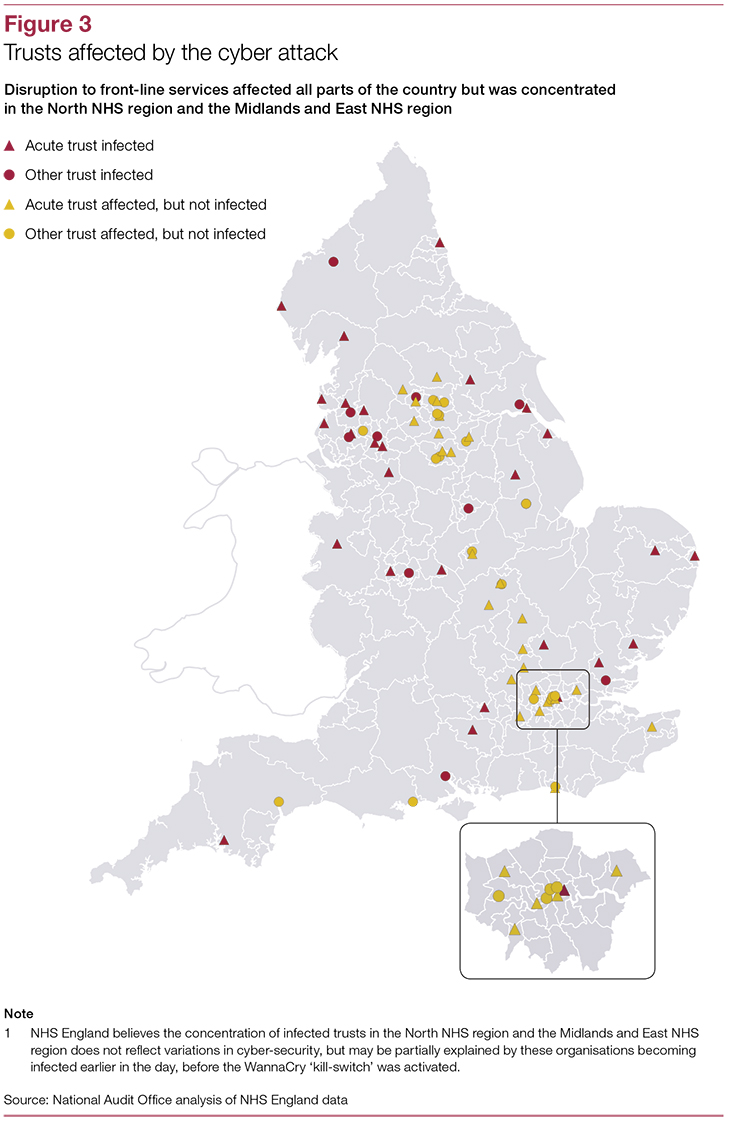
On May 12, NHS England initially identified 45 NHS organisations, including 37 trusts, that had been infected by the WannaCry ransomware. In total at least 81 out of 236 trusts across England were affected. A further 603 primary care and other NHS organisations were infected by WannaCry, including 595 GP practices. However, the report says: “The Department does not know how many NHS organisations could not access records or receive information, because they shared data or systems with an infected trust. NHS Digital told the National Audit Office that it believes no patient data were compromised or stolen.”
Thousands of appointments and operations were cancelled and in five areas patients had to travel further to accident and emergency departments. Between May 12 and 18, NHS England collected some information on cancelled appointments to help it manage the incident, but this did not include all types of appointment. NHS England identified 6,912 appointments had been cancelled, and estimated over 19,000 appointments would have been cancelled in total.
“Neither the Department nor NHS England know how many GP appointments were cancelled, or how many ambulances and patients were diverted from the five accident and emergency departments that were unable to treat some patients,” says the document.
The Department, NHS England and the National Crime Agency told the authors of the report that no NHS organisation paid the ransom, but the Department does not know how much the disruption to services cost the NHS. Costs included cancelled appointments; additional IT support provided by NHS local bodies, or IT consultants; or the cost of restoring data and systems affected by the attack.
National and local NHS staff worked overtime including over the weekend of May 13 – 14 to resolve problems and to prevent a fresh wave of organisations being affected by WannaCry on Monday, May 15.
The cyber attack could have caused more disruption if it had not been stopped by a cyber researcher activating a 'kill switch' so that WannaCry stopped locking devices, the report says.
Between May 15 and mid-September, NHS Digital and NHS England identified a further 92 organisations, including 21 trusts, as contacting the WannaCry domain, though some of these may have been contacting the domain as part of their cyber security activity. Of the 37 trusts infected and locked out of devices, 32 were located in the North NHS Region and the Midlands & East NHS region. NHS England believes more organisations were infected in these regions because they were hit early on May 12 before the WannaCry 'kill switch' was activated, according to the report.
The Department had developed a plan, which included roles and responsibilities of national and local organisations for responding to an attack, but had not tested the plan at a local level.
As the NHS had not rehearsed for a national cyber attack, it was not immediately clear who should lead the response and there were problems with communications. Many local organisations could not communicate with national NHS bodies by email as they had been infected by WannaCry, or had shut down their email systems as a precaution, though NHS Improvement did communicate with trusts' Chief Executive Officers by telephone. Locally, NHS staff shared information through personal mobile devices, including using the encrypted WhatsApp application.
NHS England initially focused on maintaining emergency care. As the attack occurred on a Friday, it caused minimal disruption to primary care services, which tend to be closed over the weekend. Twenty-two of the 27 infected acute trusts managed to continue treating urgent and emergency patients throughout the weekend.
However, five – in London, Essex, Hertfordshire, Hampshire and Cumbria – had to divert patients to other Accident and Emergency departments, and a further two needed outside help to continue treating patients. By May 16, only two hospitals were still diverting patients. The recovery was helped by the work of the cyber security researcher that stopped WannaCry spreading.
NHS Digital told the investigators that all organisations infected by WannaCry shared the same vulnerability and could have taken relatively simple action to protect themselves. Infected organisations had unpatched, or unsupported Windows operating systems so were susceptible to the ransomware. However, whether organisations had patched their systems or not, taking action to manage their firewalls facing the Internet would have guarded organisations against infection.
“The NHS has accepted that there are lessons to learn from WannaCry and is taking action,” says the report. NHS England and NHS Improvement have written to every major health body asking boards to ensure that they have implemented all alerts issued by NHS Digital between March and May 2017 and taken essential action taken to secure local firewalls.
Amyas Morse, head of the National Audit Office, noted: “The WannaCry cyber attack had potentially serious implications for the NHS and its ability to provide care to patients. It was a relatively unsophisticated attack and could have been prevented by the NHS following basic IT security best practice. There are more sophisticated cyber threats out there than WannaCry, so the Department and the NHS need to get their act together to ensure the NHS is better protected against future attacks.”
Free CRJ articles
Click here to download PDF version of Ransomware: The trap within a trap, by Todd M Rosenblum, former Principal Deputy and Acting Assistant Secretary of Defence for Homeland Defence and Americas’ Security Affairs, Deputy Under Secretary of Intelligence at the Department of Homeland Security from February 2009 – March 2015, and now Senior Executive for Worldwide Business Development at IBM. He is also President and CEO of National Security Outcomes, LLC (first published in CRJ 12:4)

Click here to download PDF version of Getting to grips with cybersecurity by Gary Fairley, former IT Security Manager in the Scottish public sector (also first published in CRJ 12:4)
